Projects
Stuff I do.
Attack-Defend CTF Launcher
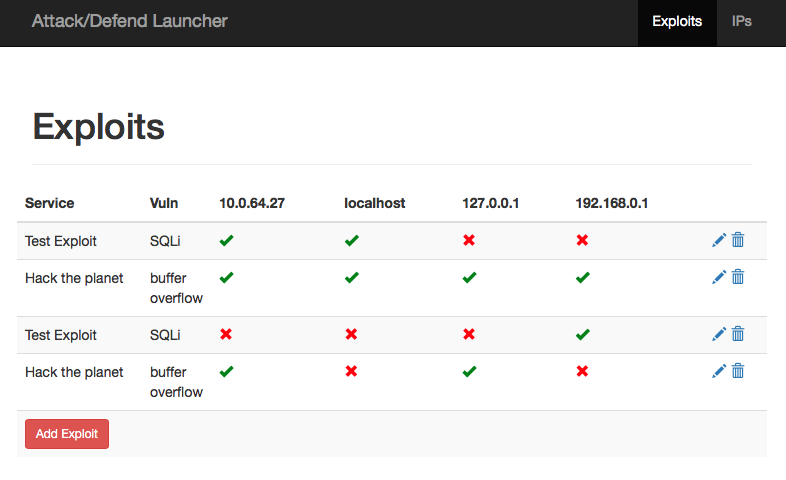
Allows teams to collaborate on a central platform to organize exploits being thrown at other teams. Exploit status refreshes in real time using websockets.
ctf_import
#include "ctf_import.h"
int main() {
int (* fib)(int);
// a.out is a binary with a fibonacci function at offset 0xf00
fib = (int (*)(int)) import("a.out", 0xf00);
printf("%d %d %d %d %d\n", fib(1), fib(2), fib(3), fib(4), fib(5));
}
A small library that allows you to run basic functions from stripped binaries cross platform.
Comic Viewer for Calvin and Hobbes

Integrates full text search, ML for comic separation, and original publish dates for an awesome Calvin and Hobbes experience.
dress

Add symbols back into a stripped ELF binary
Usage
./dress <in-file> <out-file> <sym-file> [-v]
in-file: path to the input (stripped) ELF binaryout-file: path to the desired output location of the dressed binary; this file will have the same permissions asin-filesym-file: path to the symbol file-v: turns on verbose output; this is generally not helpful unless something is going wrong
Example
$ gcc test.c
$ readelf -s a.out
Symbol table '.symtab' contains 70 entries:
...
62: 0000000000601044 4 OBJECT GLOBAL DEFAULT 26 counter
64: 0000000000400593 54 FUNC GLOBAL DEFAULT 14 main
69: 0000000000400566 45 FUNC GLOBAL DEFAULT 14 test
$ strip a.out -o b.out
$ readelf -s b.out
$ dress b.out c.out a.syms
$ readelf -s c.out
Symbol table '.symtab' contains 3 entries:
0: 0000000000601044 0 OBJECT LOCAL DEFAULT 25 counter
1: 0000000000400593 0 FUNC LOCAL DEFAULT 14 main
2: 0000000000400566 0 FUNC LOCAL DEFAULT 14 test